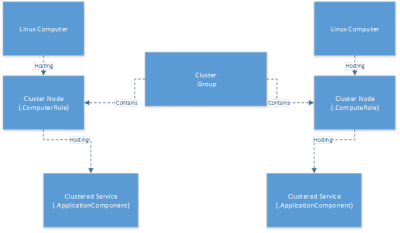
Update Rollup 5 for System Center 2012 SP1 and Update Rollup 1 for System Center 2012 R2 been released today with important Operations Manager UNIX/Linux monitoring fixes. The UNIX and Linux Monitoring Packs (and updated agents) can be found here.
The fixes for UNIX and Linux include:
System Center 2012 R2 – Operations Manager: Update Rollup 1
Issue 1
On a Solaris-based computer, an error message that resembles the following is logged in the Operations Manager log. This issue occurs if a Solaris-based computer that has many monitored resources runs out of file descriptors and does not monitor the resources. Monitored resources may include file systems, physical disks, and network adapters.
Note The Operations Manager log is located at /var/opt/microsoft/scx/log/scx.log.
errno = 24 (Too many open files)
This issue occurs because the default user limit on Solaris is too low to allocate a sufficient number of file descriptors. After the rollup update is installed, the updated agent overrides the default user limit by using a user limit for the agent process of 1,024.
Issue 2
If Linux Container (cgroup) entries in the /etc/mtab path on a monitored Linux-based computer begin with the “cgroup” string, a warning that resembles the following is logged in the agent log.
Note When this issue occurs, some physical disks may not be discovered as expected.
Warning [scx.core.common.pal.system.disk.diskdepend:418:29352:139684846989056] Did not find key ‘cgroup’ in proc_disk_stats map, device name was ‘cgroup’.
Issue 3
Physical disk configurations that cannot be monitored, or failures in physical disk monitoring, cause failures in system monitoring on UNIX and Linux computers. When this issue occurs, logical disk instances are not discovered by Operations Manager for a monitored UNIX-based or Linux-based computer.
Issue 4
A monitored Solaris zone that is configured to use dynamic CPU allocation with dynamic resource pools may log errors in the agent logs as CPUs are removed from the zone and do not identify the CPUs currently in the system. In rare cases, the agent on a Solaris zone with dynamic CPU allocation may hang during routine monitoring.
Note This issue applies to any monitored Solaris zones that are configured to use dynamic resource pools and a “dedicated-cpu” configuration that involves a range of CPUs.
Issue 5
An error that resembles the following is generated on Solaris 9-based computers when the /opt/microsoft/scx/bin/tools/setup.sh script does not set the library pathcorrectly. When this issue occurs, the omicli tool cannot run.
ld.so.1: omicli: fatal: libssl.so.0.9.7: open failed: No such file or directory
Issue 6
If the agent does not retrieve process arguments from the getargs subroutine on an AIX-based computer, the monitored daemons may be reported incorrectly as offline. An error message that resembles the following is logged in the agent log:
Calling getargs() returned an error
Issue 7
The agent on AIX-based computers considers all file cache to be available memory and does not treat minperm cache as used memory. After this update rollup is installed, available memory on AIX-based computer is calculated as: free memory + (cache – minperm).
Issue 8
The Universal Linux agent is not installed on Linux computers that have OpenSSL versions greater than 1.0.0 if the library file libssl.so.1.0.0 does not exist. An error message that resembles the following is logged:
/opt/microsoft/scx/bin/tools/.scxsslconfig: error while loading shared libraries: libssl.so.1.0.0: cannot open shared object file: No such file or directory
System Center 2012 SP1 – Operations Manager: Update Rollup 5
Issue 1
In rare cases, the agent on a Solaris Zone that is configured to use dynamic CPU allocation with Dynamic Resource Pools may hang during routine monitoring.
Note This issue can occur on any monitored Solaris Zone that is configured to use Dynamic Resource Pools and a “dedicated-cpu” configuration that involves a range of CPUs.
Issue 2
If the agent fails to retrieve process arguments from the getargs subroutine on an AIX-based computer, the monitored daemons may be incorrectly reported as offline. An error message that resembles the following is logged in the agent log:
Calling getargs() returned an error
.
Issue 3
The agent on AIX-based computers considers all file cache to be available memory and does not treat minperm cache as used memory. After this update rollup is installed, available memory on AIX-based computer is calculated as: free memory + (cache – minperm).
Issue 4
The Universal Linux agent fails to install on Linux computers with OpenSSL versions greater than 1.0.0 if the library file libssl.so.1.0.0 does not exist. An error message that resembles the following is logged:
/opt/microsoft/scx/bin/tools/.scxsslconfig: error while loading shared libraries: libssl.so.1.0.0: cannot open shared object file: No such file or directory
Issue 5
Spurious errors that are related to the InstanceID property of the SCX_Endpoint are logged in the System log every four hours.